Sherlocks: UFO-1
Hack The Box
Hello, everyone! Today, we’ll be exploring the Sherlock UFO-1 from Hack The Box. This challenge is categorized as Very Easy under the Threat Intelligence section. It involves conducting research and intelligence gathering on APT44, also known as Sandworm Team or BlackEnergy Group.
To analyze this adversary, we’ll utilize the MITRE ATT&CK framework to map out their tools, techniques, and procedures.
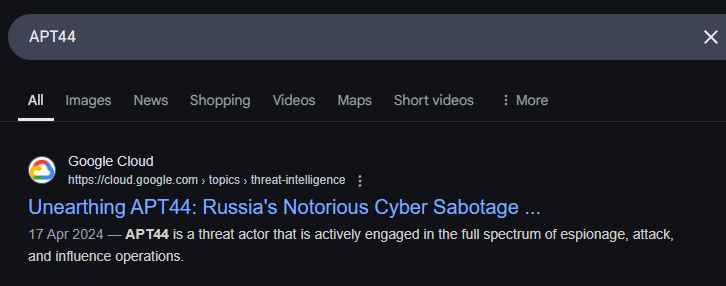
Before diving into the questions, let’s first explore who Sandworm Team is and what their objectives are. A quick Google search for “APT44” leads us to an excellent threat intelligence blog by Google’s Mandiant, titled "Unearthing APT44: Russia’s Notorious Cyber Sabotage Unit Sandworm." This article provides a great overview of how this threat group operates.
The blog also includes a detailed report titled “APT44: Unearthing Sandworm,” which provides an in-depth analysis of the Sandworm Team. I highly recommend reading this report before attempting to answer any questions in this Sherlock.
Before we proceed, I want to emphasize the importance of collecting and analyzing information as a Threat Intelligence Analyst. For those unfamiliar with the field, intelligence work involves extensive reading and research. The cyber threat landscape is constantly evolving, and threat actors continuously adapt their tactics, techniques, and procedures (TTPs). To stay ahead, cybersecurity professionals must regularly study reports and analyze data—raw information alone is not enough.
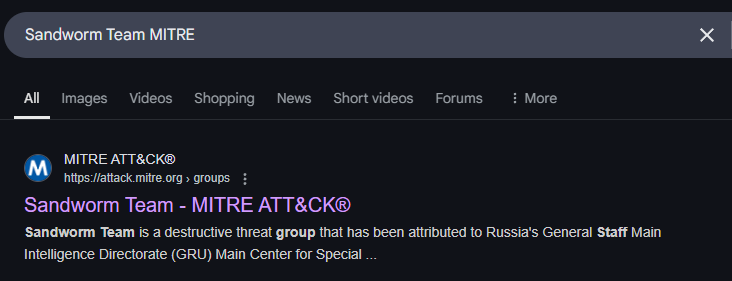
Moving forward, we will primarily use MITRE ATT&CK to answer most of the questions in this Sherlock. Let’s start by performing another Google search for “Sandworm Team MITRE” and navigating to the website.
Task 1
According to the sources cited by MITRE, in what year did the Sandworm Team begin operations?
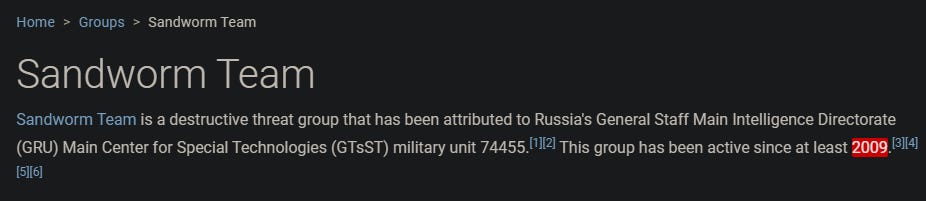
According to both the Mandiant report and MITRE, the Sandworm Team has been active since 2009.
Answer: 2009
Task 2
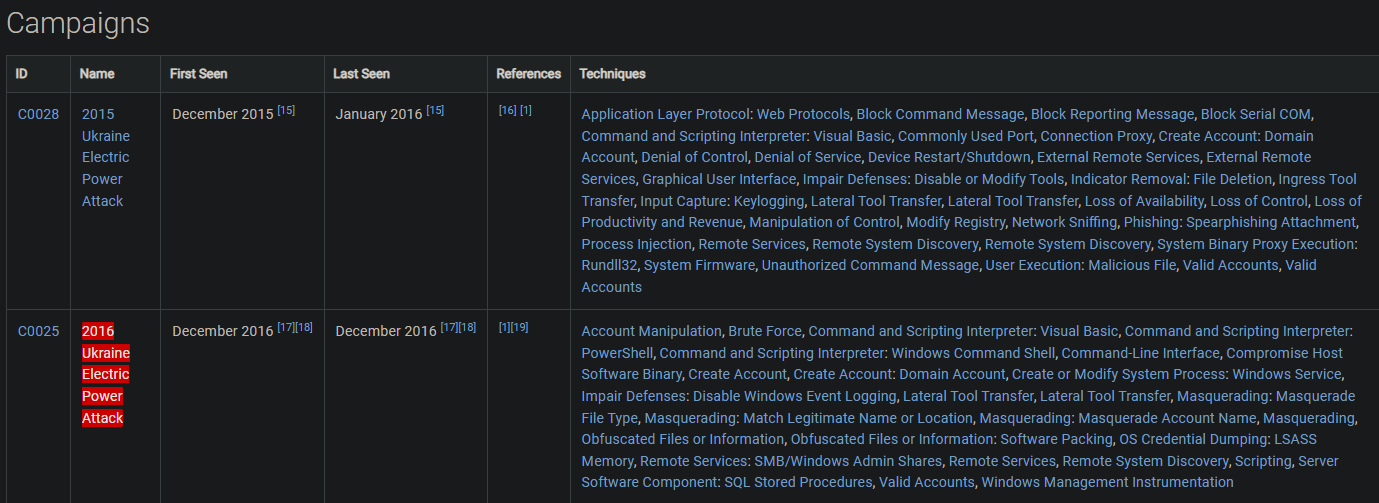
MITRE notes two credential access techniques used by the BlackEnergy group to access several hosts in the compromised network during a 2016 campaign against the Ukrainian electric power grid. One is LSASS Memory access (T1003.001). What is the Attack ID for the other?
Scroll down to the "Campaigns" section and look for any campaigns from 2016.
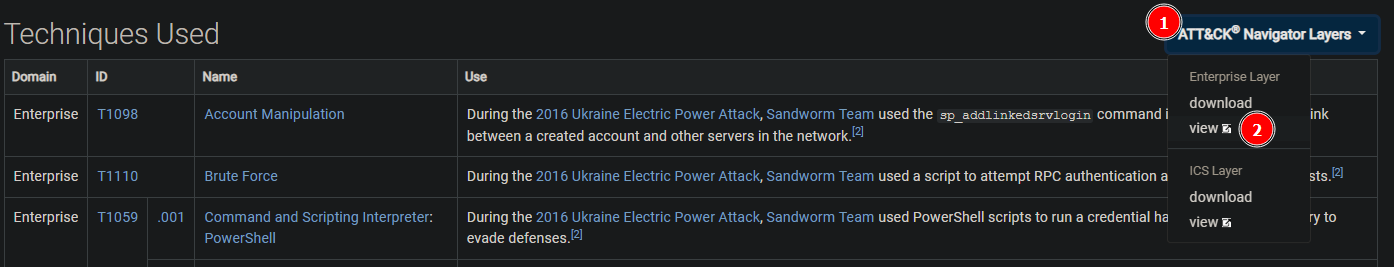
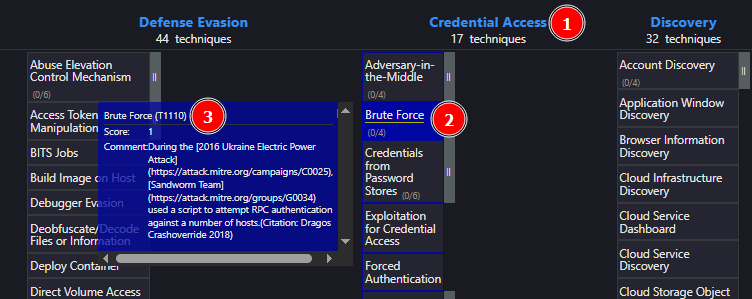
On the Campaigns page, we will use the ATT&CK Navigation Layers [1], then click the "View" option [2] to locate Credential Access techniques.
Go to the "Credential Access" tab [1], then look for the highlighted "Brute Force" technique [2]. There, you’ll find the Attack ID [3].
Answer: T1110
Additional Notes: Here is a conference paper on the 2016 Ukraine Electric Power Attack, titled “Ukraine Cyber-Induced Power Outage: Analysis and Practical Mitigation Strategies.”
Task 3
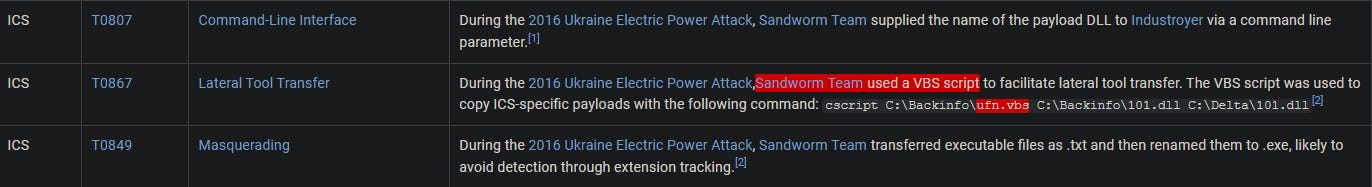
During the 2016 campaign, the adversary was observed using a VBS script during their operations. What is the name of the VBS file?
Navigate back to the 2016 Ukraine Electric Power Attack campaign page and search through the techniques used. Look for any mention of the .VBS file—here, we see it listed under the "Lateral Tool Transfer" technique.
Answer: ufn.vbs
Task 4
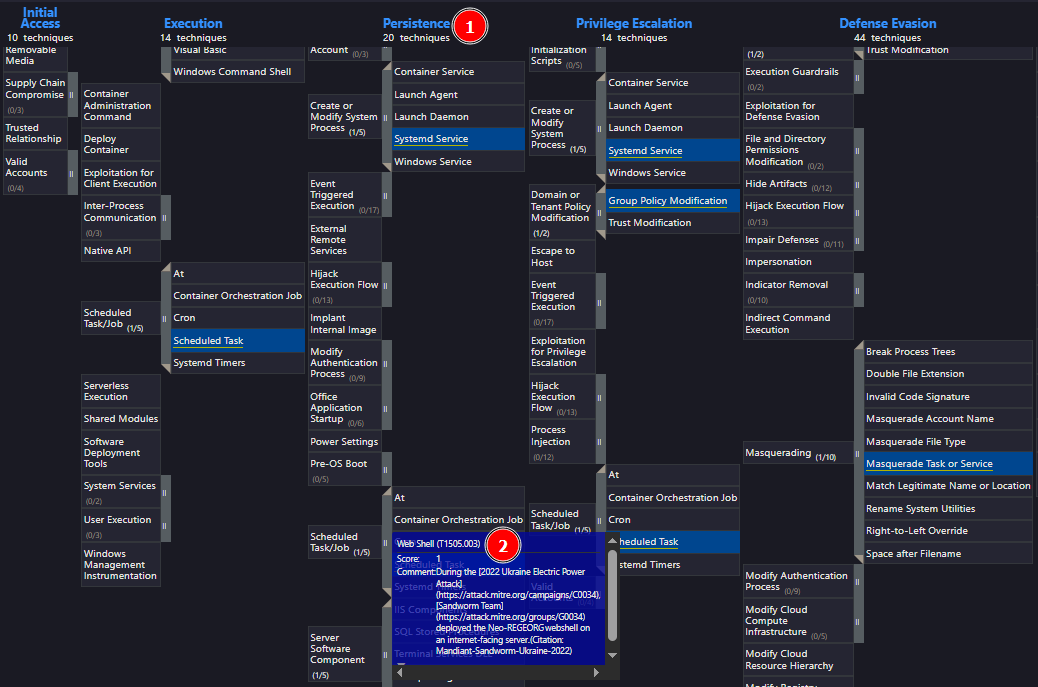
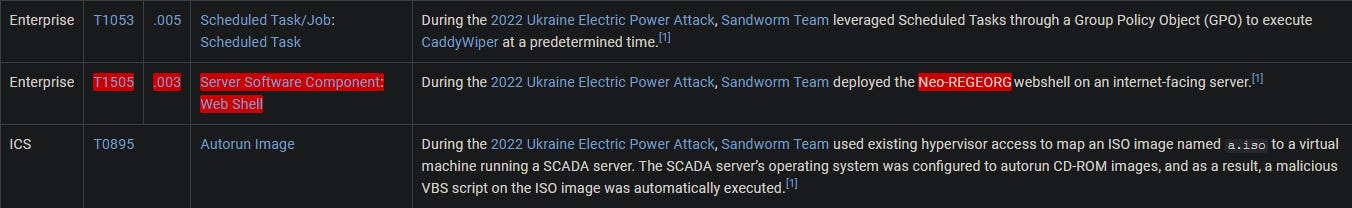
The APT conducted a major campaign in 2022. The server application was abused to maintain persistence. What is the MITRE ATT&CK ID for the persistence technique was used by the group to allow them remote access?
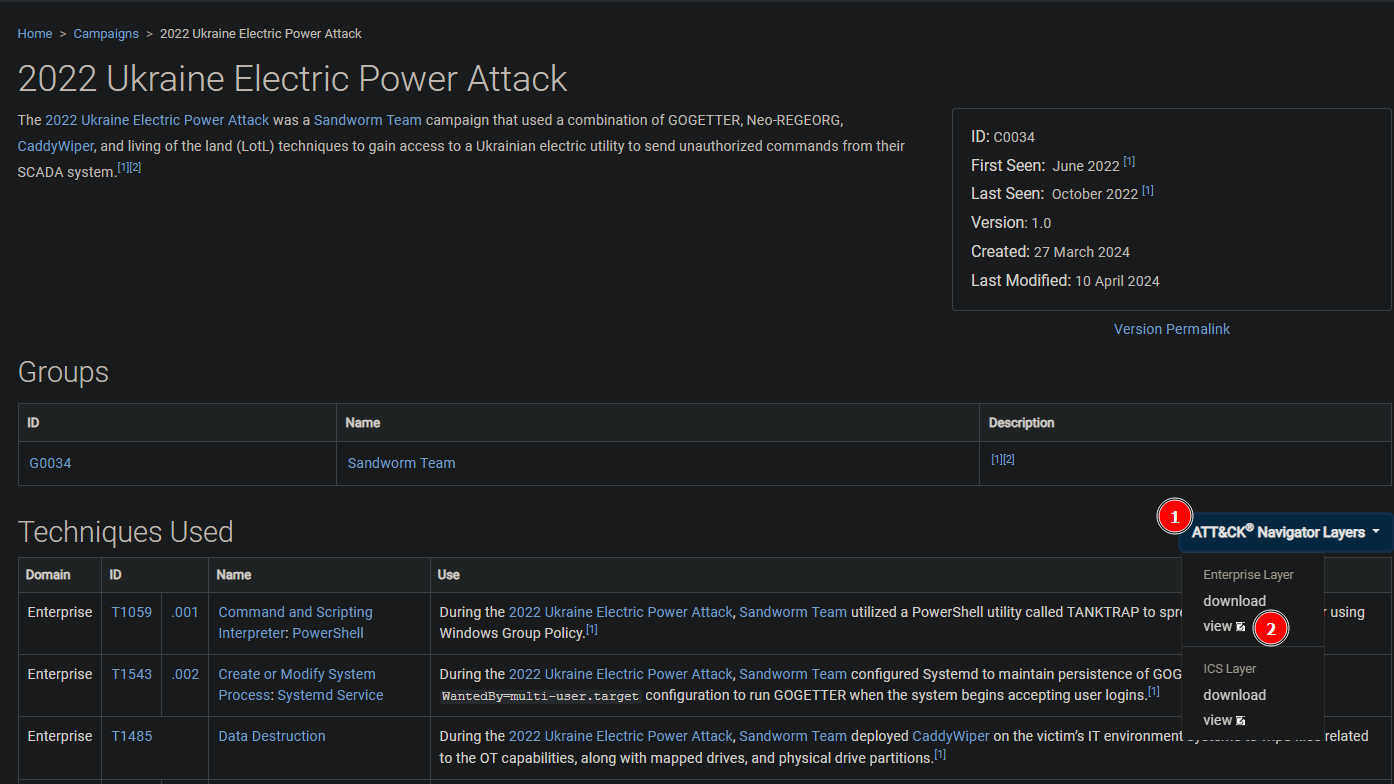
Returning to the Sandworm Team group page, we find the 2022 Ukraine Electric Power Attack campaign. Late in 2022, Sandworm Team escalated its cyberwarfare efforts against the Ukrainian power grid. In this instance, they used the "Server Software Component Web Shell" technique to maintain persistence in the system.
Open the ATT&CK Navigator [1] on the 2022 campaign page and view the Enterprise layer [2], just as we did in Task 2.
Under Persistence [1], look for the highlighted sub-technique labeled "Web Shell" [2] to find the Attack ID.
Answer: T1505.003
Task 5
What is the name of the malware / tool used in question 4?
In question 4, we highlighted the sub-technique used, and there we see the deployed “Neo-REGEORG” Web Shell. To confirm this, we can also return to the 2022 Ukraine Electric Power Attack campaign page and find it listed under the Techniques table.
Answer: Neo-REGEORG
Task 6
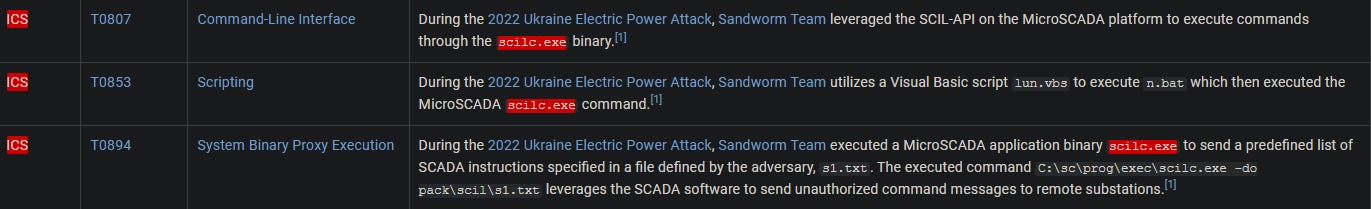
Which SCADA application binary was abused by the group to achieve code execution on SCADA Systems in the same campaign in 2022?
For some context, SCADA stands for Supervisory Control and Data Acquisition. SCADA systems enable companies to monitor and manage complex industrial operations that may span large areas. SCADA is a type of Industrial Control System (ICS), but it specifically focuses on large-scale, distributed control systems.
In the technique matrix, we should navigate down to the ICS domain. In this case, we are looking for a specific binary that was abused, and here we see it mentioned multiple times.
Answer: scilc.exe
Task 7
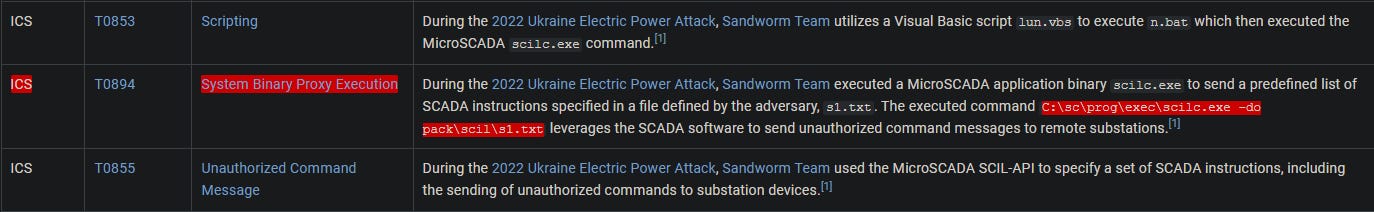
Identify the full command line associated with the execution of the tool from question 6 to perform actions against substations in the SCADA environment.
Here, we’re looking for any command-line executions. In this case, we see:
Answer: C:\sc\prog\exec\scilc.exe -do pack\scil\s1.txt
Task 8
What malware/tool was used to carry out data destruction in a compromised environment during the same campaign?
As we navigate further down the page to the software matrix, we see only one tool listed.
Answer: CaddyWiper
Task 9
The malware/tool identified in question 8 also had additional capabilities. What is the MITRE ATT&CK ID of the specific technique it could perform in Execution tactic?
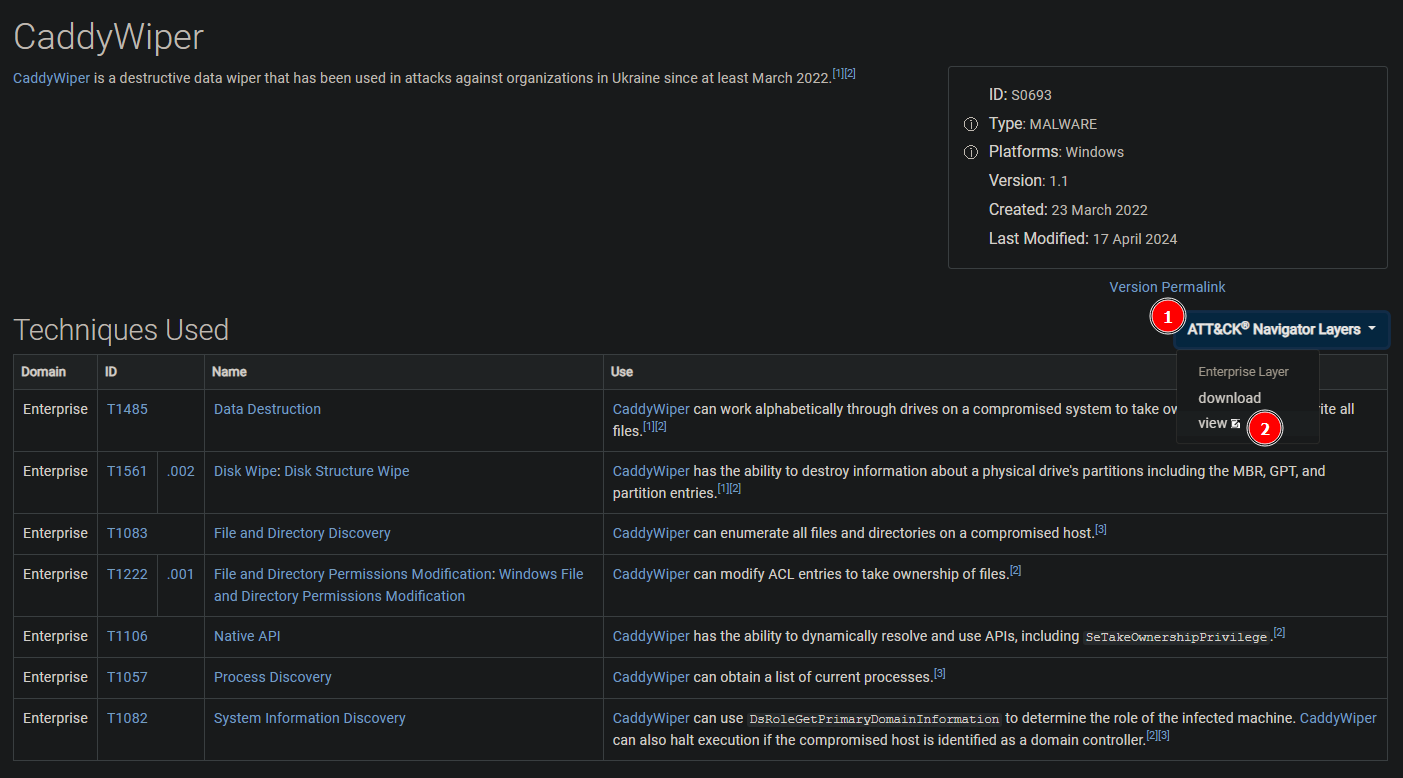
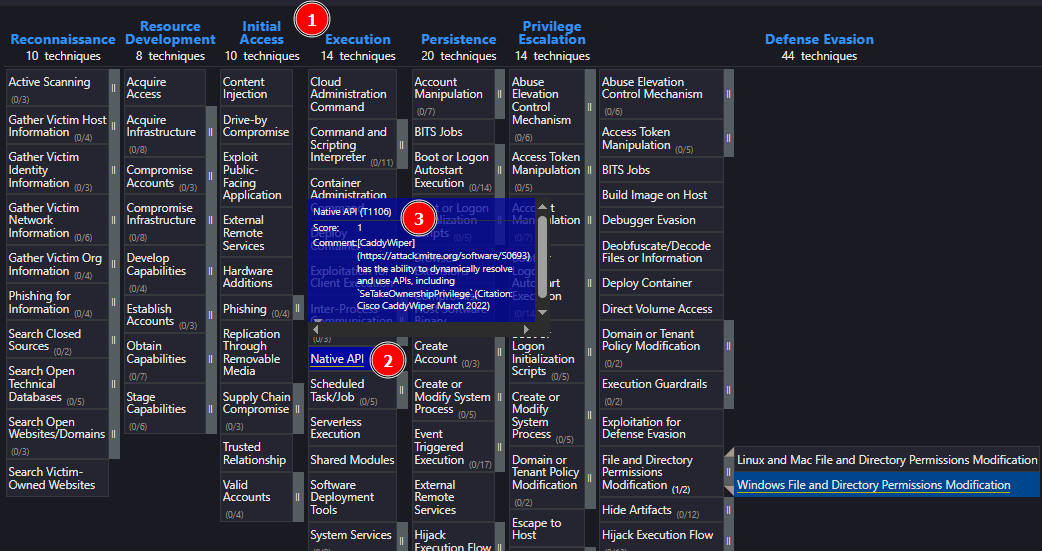
Let’s navigate to the CaddyWiper software page, open the ATT&CK Navigator [1], and view the Enterprise Layer [2].
In the Execution technique matrix, we see "Native API" highlighted. This shows that CaddyWiper is able to abuse the Windows Native API. Additionally, we see that it can exploit the user right “SeTakeOwnershipPrivilege”, which allows CaddyWiper to take ownership of system objects and modify access permissions. Palantir has published an excellent blog on Windows Privilege Abuse, which is worth checking out for a deeper understanding.
Answer: T1106
Task 10
The Sandworm Team is known to use different tools in their campaigns. They are associated with an auto-spreading malware that acted as a ransomware while having worm-like features. What is the name of this malware?
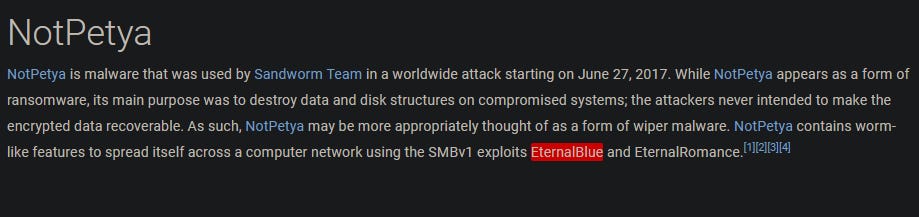
One of the most famous tools listed in the software matrix is NotPetya. Not only did it function like ransomware, but it was also a wiper disguised as ransomware. In addition to being a wiper, it had additional functionality that allowed it to propagate using EternalBlue. The researchers at Crowdstrike have published a detailed technical analysis of this tool.
Answer: NotPetya
Task 11
What was the Microsoft security bulletin ID for the vulnerability that the malware from question 10 used to spread around the world?
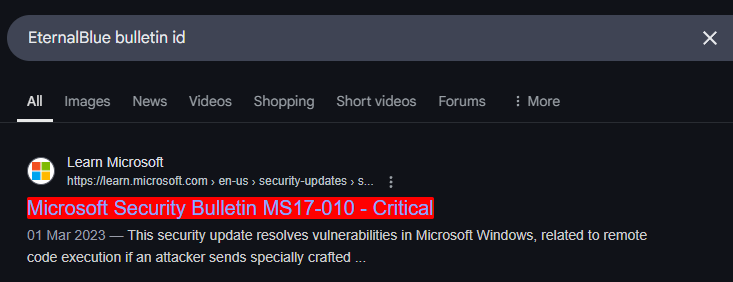
When viewing the NotPetya tool profile on MITRE, we can see that the description mentions the abuse of SMBv1 with EternalBlue.
Let’s take this information and perform a Google search for the Bulletin ID for EternalBlue. The first result immediately shows our Bulletin ID.
Answer: MS19-010
Task 12
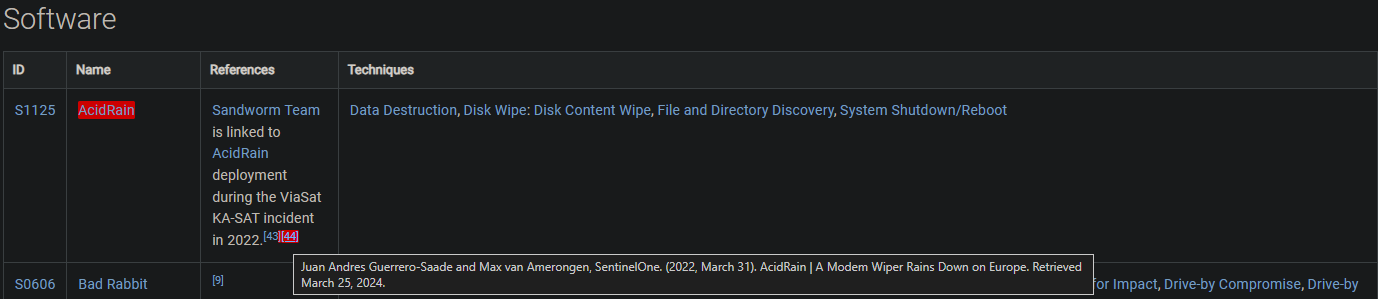
What is the name of the malware/tool used by the group to target modems?
When viewing the references in the Software tool matrix, we see only one specific mention of "modems." In this case, it’s AcidRain, listed under reference [44].
Answer: AcidRain
Task 13:
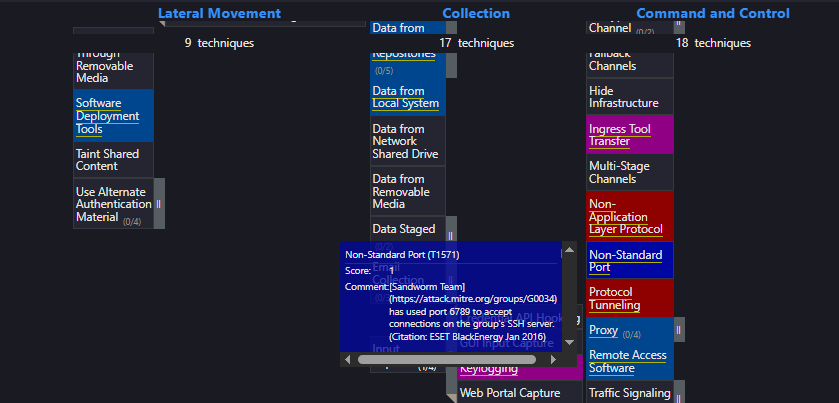
Threat Actors also use non-standard ports across their infrastructure for Operational-Security purposes. On which port did the Sandworm team reportedly establish their SSH server for listening?
To answer this, we’ll need to navigate back to the Enterprise Layer matrix. Then, apply a "find" filter (Ctrl+F) to search for "Non-Standard Port." We find one result under Command and Control, where the port listed in the matrix is 6789.
Answer: 6789
Task 14
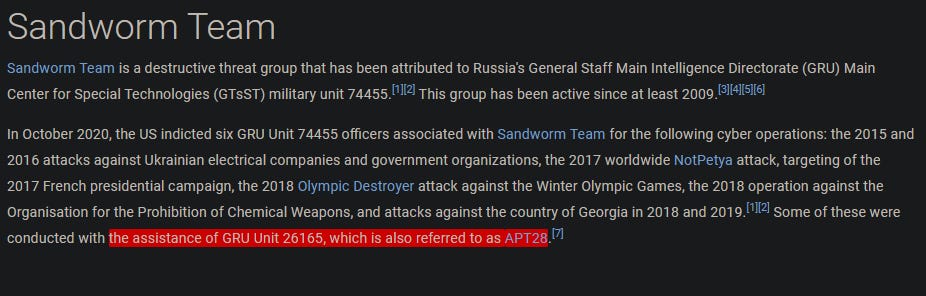
The Sandworm Team has been assisted by another APT group on various operations. Which specific group is known to have collaborated with them?
If you recall, there was mention of another group in the Sandworm Team profile introduction. We can find the name of the group in the description: APT28, also famously known as Fancy Bear.
Answer: APT28
And that’s a wrap, folks! I hope you learned and enjoyed this as much as I did. Until next time! :)